Cryptography is critical to modern information security. In addition to resisting overt attack, cryptographic systems must also be resilient against sabotage and covert weakening. These more surreptitious attacks can include errors built in to cryptographic systems in the design stages, or vulnerabilities introduced during implementation or later. There is a desire to better understand how unknown weaknesses in cryptographic systems are successfully exploited, beyond a description of how past attacks have been performed.
One way of understanding similarities and differences is to arrange examples according to specific properties. A taxonomy is a set of consistent rules for organizing content. Schneier et al. create a taxonomy to describe the properties of cryptographic weaknesses. Secrecy, utility, and scope are the three major domains of weakness. Each domain has several components that can be used to characterize a weakness in more detail.
When these factors are present and strong, the attacker is more likely to be successful. These dimensions can be used to explore historic cases of cryptographic weaknesses that were successfully exploited. When the taxonomy is used to categorize examples of attacks, it is possible to see patterns. An example is seen in the tradeoffs faced by a saboteur. For example, if precision in targeting and control over who shares access to the weakness are high, conspiracy must also increase, which reduces deniability. The taxonomy can also be applied to look at attack approaches more abstractly. What are the characteristics of various strategies, such as building in a low resistance to cryptanalysis or choosing backdoor constants, and of flawed implementation approaches, such as involving bad randomness or leaking key data?
This analysis reveals strategies to minimize weakness and defend against cryptographic sabotage:
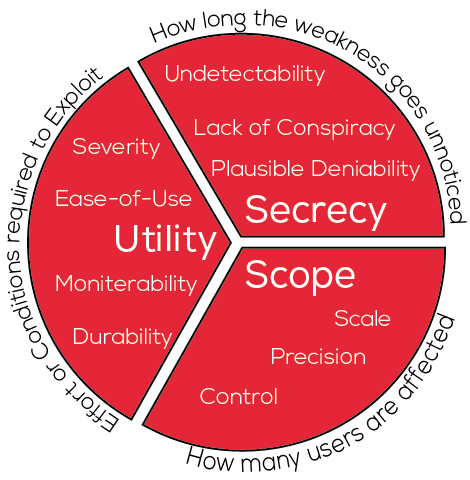
Cryptographic weakness taxonomy helps identify potential forms of exploitation and assist choosing an encryption scheme that is suited to a particular need