Location-based services prevent or facilitate access or actions online, such as media streaming, online voting or gambling, fraud prevention based on the physical location of the requesting party. Delay-based techniques of location detection are gaining support as they offer increased reliability when compared to other techniques such as requesting the location from the clients (e.g. GPS) or tabulation-based IP geolocation services. However, this increased reliability may not be sufficient basis for their use in security contexts.
Abdou, Matrawy, and van Oorschot explain new attack techniques that enable adversaries to accurately manipulate the location indicated by these delay-based techniques. They devise new strategies that allow adversaries to fake their location without knowing the delay-to-distance mapping function of the delay-based location detection service.
A sender can measure the delay between itself and a receiver by having the receiver respond to special data packets and timing the responses. This is achieved by recording the time the packet was sent, either in the message itself or in the sender’s memory and comparing that with the time that the packet is returned. By selectively manipulating the delay of these packets in a precise manner an adversary would be able to appear to be in a different location. The difficulty lies in modeling the expected delays to accurately match an intended location precisely enough to fool the location detection system.
The researchers presented techniques based on a variety of attacker scenarios, altering the capacity and information available to each. The novel methods developed by the researchers would be able to able to model delays with sufficient accuracy for a theoretical attacker based in continental Europe to fake a location in the United States of America.
This work makes clear the importance of security not relying on measurements that lack integrity. The measured delays used for location services are able to be manipulated. Security-sensitive applications should not rely on constrained region areas for distinguishing legitimate clients.
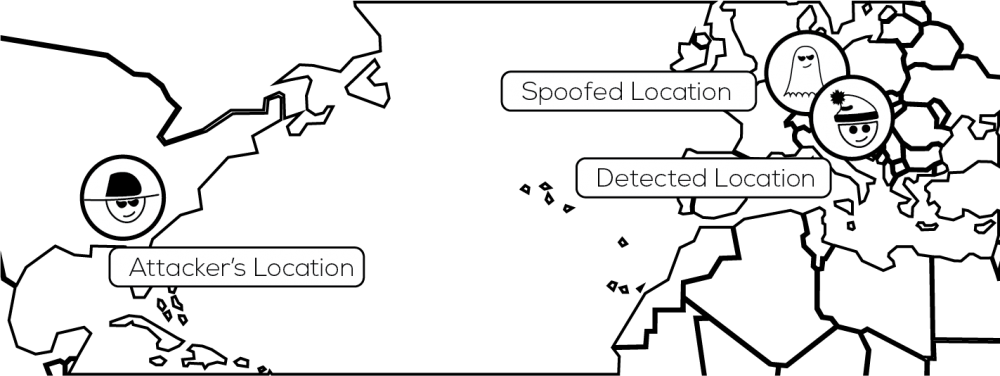
Location detection services are not reliable enough for security purposes.