Attribution is fundamental to cyber security. An appropriate response to any cyber offence requires first identifying the offender. Finding ‘who did it?’ is often seen as a purely technical problem, a puzzle to be solved with forensic evidence. Attribution in digital forensics faces some added challenges because of the mythology surrounding cyber capacity. It is important that attackers are not allowed to operate with an expectation of anonymity. This anonymity is a myth; even if the attribution problem cannot be solved, it can be managed.
Attribution problems are fundamentally different to those of cyber security. The large scale of connected industry and infrastructure can be seen as a vulnerability – an expansive attack surface – but developed nations have the advantage of resources for identifying and concealing cyber operations. Further, the pressure for constant precision is transferred from the defender to the attacker, as a single mistake can be sufficient for attribution. The quality of attribution is a function of the available time, available resources and the adversary’s sophistication. But attribution is not just a question of traces revealed in technology. Like any investigation, there are pressures to maintain reputations and affiliations on a larger scale. Investigating cyber attacks fully requires coordinating multiple specialties, proceeding through judicial levels, and prevailing in legal proceedings against competing evidence.
Rid and Buchanan developed the ‘Q Model’ to illustrate the complexity of the process of attribution. This model collects the aspects of an investigation into a unified framework, which provides context and shape, as well as a checklist of things to watch for in investigations. The model distinguishes three levels of analysis, as shown below.
Each level relies on different sources of information for analysis, but success depends, in part, on strong communication between the levels. The degree of uncertainty and use of assumptions with judgment may increase as analysis moves away from the tactical and technical level.
This model can be applied in practice across many levels of an investigation. It is important to
The Q Model emphasizes the need to question the results of an investigation or attribution process. This safeguard is built in, with communication between the levels. Communication also extends beyond the layers of the investigation to the surrounding space; law enforcement tend towards secrecy, but communicating with stakeholders can increase credibility, enhance the quality of the outcome, and strengthen defenses. This is with the clear caveat that any communication must emphasize the gradual nature of the attribution process and the degree of uncertainty that remains.
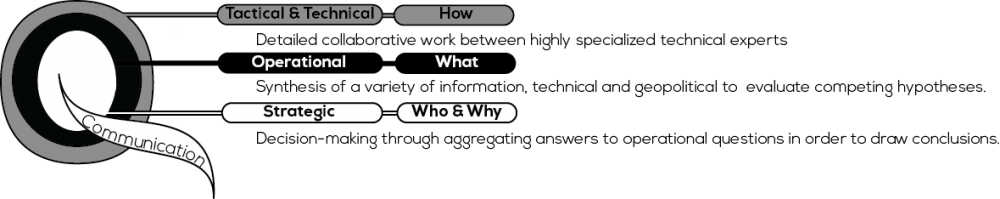
Attributing cyberattacks is a complex art that combines technical, operational and strategic level investigations with managed communications in a delicate process over time.