Do cybercriminals meet and collaborate differently? Friends, family and other social contacts are often how criminal groups start. To grow in capacity these groups look outside of their existing social circle. Criminals could only expand their network by meeting contacts in appropriate physical spaces; such as cafés and bars. The Internet provides spaces to connect virtually that are both appropriate and specific to various forms of criminal activity. Criminals can exchange information, learn skills, find support and form relationships in dedicated online forums. However, the existence of Internet relationships does not preclude real world social connections.
Leukfeldt, Kleemans and Stol studied police investigation reports on online banking offenses, such as theft of personal information by phishing and malware to gain a better understanding of the social relationships within cybercrime networks. They looked at the network origins and growth, the relationships between members as well as the role of forums within the network. The researchers studied 18 police files on online banking crimes. Ten were phishing attacks, five were malware attacks and three cases combined both phishing and malware attacks. The cases studied included information from recorded phone calls and Internet traffic, undercover observation, house searches and interviews. Group members were seen as performing one of three roles. ‘Core members’ initiated and coordinated the attacks: without them, no crime would be planned. ‘Enablers’ provided the services and technical skills necessary for the crime to happen. Finally, ‘money mules’ disguised the financial trail left by the crime.
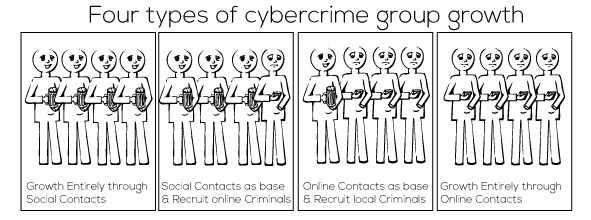
70% of the networks grew solely through social contacts, with forums being used only to obtain specific knowledge or tools. Core members recruited enablers from among their family or acquaintances, at sports clubs, schools or on the street. The number and types of enablers that they could use were limited. Enablers recruited were often used for multiple activities out of necessity. 10% of the networks grew from a base of social contacts, but used forums to recruit specialists. They used forums to purchase specific illegal services or products such as mailing lists or malware. One network grew from an online group to include social contacts. Although tools and techniques were acquired and discussed primarily through the Internet, social contacts were used to recruit locals offline as money mules or as service company insiders to overcome security. 10% of networks recruited entirely through forums. They found specialists online, from whom they purchased services and products. They were also able to recruit money mules through spam mailing campaigns.
Social contacts were used to form or grow the majority of the groups studied. However, online forums do impact how groups operate as they seem to make it easier to find accomplices with specific talents and are a key source of criminal knowledge and skills.
Real world social connections are still very important for cybercriminal networks, but online interaction helps with knowledge acquisition.