The evolving world of information technology raises new issues for securing networks. Many enterprises offer a Bring-Your-Own-Device (BYOD) environment, which supports users who choose to take their own technology, like laptops and smartphones, to work and use them on a secured network. More recently cloud- and web-based services have allowed users to move applications seamlessly between computing environments. In a Bring-Your-Own-Application (BYOA) context companies encourage the use of consumer products such as personal applications in the workplace. This is often an extension of BYOD, one which also permits personnel to choose their software for getting their work done. Existing institutional and corporate policies for BYOD may not be enough to manage, and may even conflict with, this emerging BYOA practice.
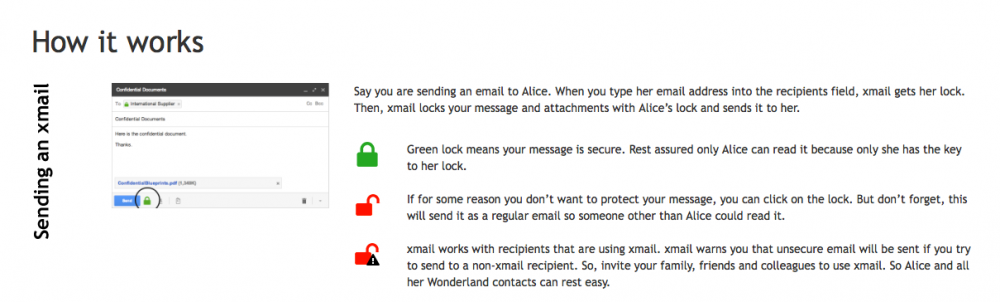
Hecht et al. examined an always-on approach to usable security that could be applied in a BYOA environment. The goal was to test a non-intrusive and easy to use portable encryption method which showed the security of communications using an open and closed lock metaphor. Seventy-two participants downloaded and used the alternative encryption plug-in for webmail clients, such as Google’s Gmail, on the Chrome browser. The researchers collected public user data from these participants and followed up with interviews of the 29 users who could be reached to provide feedback.
The always-on, plug-in approach is a promising solution but some issues remain. Users were successful in exchanging emails securely and were able to understand the lock and key metaphor used in the experiment. However, users expected greater flexibility in the implementation of the security features, due to a variety of email practices. In particular BYOA security solutions must permit users to:
This study demonstrated that users will not compromise usability for security in their webmail usage. For example, users want the ability to search all messages, even protected ones. This, however, conflicts with the encryption provided by the experimental plug-in. To be successfully adopted, security protocols must match these types of expectations for usability. This study demonstrated the need for comprehensive institutional and corporate BYOA policies that can meet evolving day-to-day practices such as use of popular webmail clients to manage all emails.
Users bringing their own applications to work creates security issues. Solving these issues isn’t simple as users will not accept add-on security at the expense of utility.