A large number of security and forensic applications, especially in a cloud environment, rely on the fingerprinting of executable code. There are many ways of combining lines of programming instructions or code to achieve a result. This creates unique patterns of code, which much like a fingerprint can be used for more reliable identification. The goal of this study is to support security and management services in largescale virtualized environments by enhancing the ability to identify code regardless of where it is .
Ahmed et al. present primary research on a technique to identify a known piece of code that is running in an arbitrary location. The authors developed a research prototype, and evaluated its effectiveness on more than 50,000 samples of executable programs.
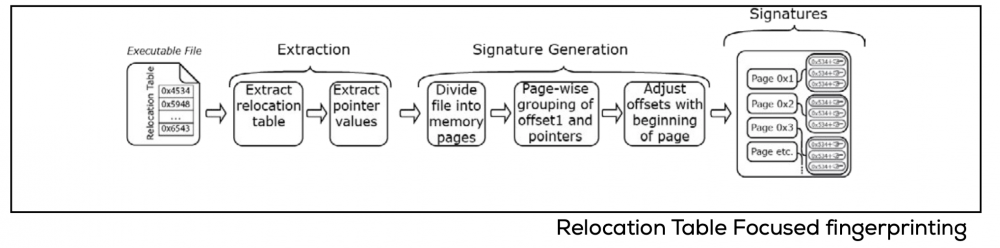
The authors recognized that previous fingerprinting techniques for Microsoft Windows were not able to work with partial information and required an expert analyst to drive the discovery process. To overcome this problem they proposed a new solution using relocation tables (a directory of where each executable code is located) as the key identifying characteristic. Relocation tables have inherent patterns that are quite distinct, which can be used accurately and efficiently to identify known executable code.
The method starts by dividing an executable file into smaller blocks, with each block given a generated signature (fingerprint). A block signature consists of relocations in the code and the offset values for the relocations. These signatures are quite unique and can be easily identified in the relocation tables. The only input required to generate a signature is the file containing the executable code. Empirical results show nearly 100% accuracy when identifying fingerprints. Essentially, this technique and tool can find a segment of executable code that has been moved by identifying the fingerprint left in the relocation table.
Identifying executable code is an important aspect of security monitoring and forensic analysis. The research provides another tool for code identification, which will become increasingly important in complex environments and investigations. Although malware detection and classification was not the purpose of this study, the method can be applied to finding known malware executables.
There is a growing trend towards cloud providers offering ever more sophisticated security-related services for their tenants. This research could provide enhanced abilities to providers by offering a robust method for automated fingerprinting.
Fully automated and feasible code identification through fingerprinting is possible, providing promise of new tools for security professionals.