Distributed Denial of Service (DDoS) attacks overload computers until they are unable to operate properly. Online gamers use DDoS attacks to attack their opponents by disrupting their Internet connection or the game itself. This is known as ‘booting,’ where players ‘boot’ or remove other players from the game. There is a demand for DDoS attack services and they are provided by websites called ‘booter services.’ Although there have been studies on the size of the booter market and on individual services, there is a need to explore the backstories of booter service providers.
Hutchings and Clayton wanted to understand more about the individuals behind booter service providers. Their goal was to listen to booter service providers talk about their own lives and activities. The researchers invited booter service providers with publicly accessible websites to take part in a survey. The service providers studied mainly used amplification techniques to overload computers. These techniques exploit a feature of network traffic management to amplify their attack capacity. This allows them to generate enough traffic to overwhelm systems without using a botnet. The researchers communicated with the operators of 63 openly advertised booter services. 13 booter service providers decided to take part in the study. The participants had the opportunity to either fill out an online survey or take part in an interview.
The researchers found that there is a gradual path to becoming a booter services provider. The participants were generally young, male, and influenced by their peers. Many started using booter services as gamers and hackers and became acquainted with the provision of booter services through friends and online communities. Some participants viewed providing booter services as a way to learn new skills. Despite clear indications of illegal use, they tended to deny that they were providing illegal or harmful services, claiming instead that they offered an important service for network testing.
In general, they advertised their services on platforms similar to those that first introduced them to booting, such as hacker forums and social media. Booter service providers did not seem to be concerned about law enforcement. Their greatest source of frustration was in receiving payment for their services, as Internet transaction companies such as PayPal had disrupted payments to booter service providers from time to time.
Running booter services is currently considered ‘easy money,’ with little cost in terms of time spent maintaining the sites. The spectre of legitimacy even allows sites to engage large third party companies such as CloudFlare for security to reduce the impact of unfriendly competition. Their main frustration at the moment is receiving payment, since some companies reject their claims of legal operation and deny them service.
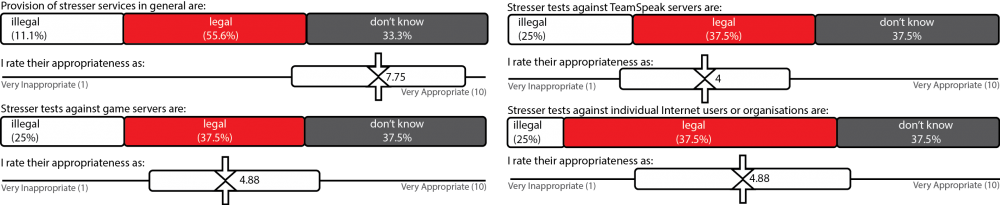
Attackers view booter services as profitable, low effort and low risk since they are not often targeted by law enforcement.