In the US military, roles are separated by function. Liles and Kambic weigh the impact of this structure for cyber defence. When layered with intentional secrecy of military operations, the result is a breakdown in the flow of information. Silos are not uncommon in communication within organisations, but the stakes are particularly high when the mandate includes offensive and defensive action intended to cause harm. One of the outcomes of this ineffective information flow can be accidental material harm to an ally. Cyber fratricide is the unintentional interference between operational or tactical elements of friendly forces involving the compromise or liquidation of assets, information, or capabilities of those forces.
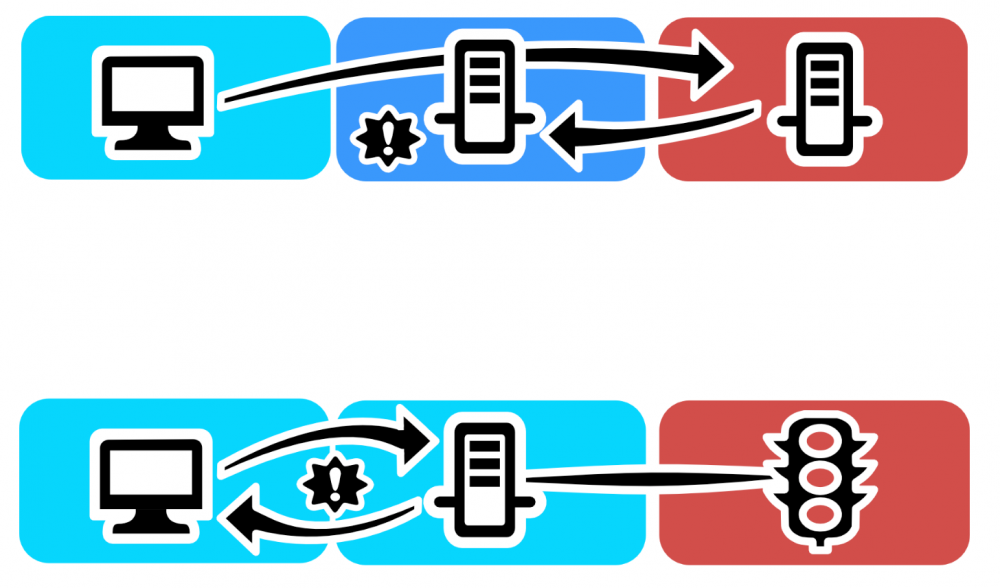
Operations in the cyber realm may be more vulnerable to this sort of interference. Cyber exchanges are, by nature, transactional, unlike other forms of access or observation. This means that connections created for observation and action in cyberspace may allow an adversary observation and action back into the instigating organisation. So the observer cannot use their own network connections to conduct an attack and must equally be cautious about use of other allied networks.
Routing operations through friendly servers can create conflict between cooperative interests. For example the friendly party (shown in the middle) may identify unauthorised use and deploy countermeasures, or the target (red, on the right) may retaliate or block connections, thus placing friendly parties at risk. Minimal action in any direction can compromise the integrity of the infrastructure. In addition to possibly infecting, attacking, or degrading service to friendly nodes during execution of the attack, an attack may incidentally grant enemy access to the network or destroy friendly assets in the course of defensive duties.
Further complications can also arise. In the hypothetical scenario where a Traffic Management System (TMS) is exploited to create tactical advantage for ground forces, it is very possible that the TMS service administration is outsourced, even to a firm within the friendly territory. Actions to compromise that system could be considered as a war crime as military actions launched against civilian parties. Furthermore any security measures employed by that firm could be considered as acts of treason as they would aid the adversary.
The current method of defining area of operation for cyber is underdeveloped: “Without a mapping function that allows for holistic situational awareness and targeting of cyber assets both physically and logically, the current construct for area of operation is not only incomplete and ineffectual” (p337). Such a mapping function would increase the accuracy of engagement. Creating more assessment and feedback points in operational phases would improve agility and situational awareness particularly when feeding in assessments from prior information operations. Redefining duties of established positions would also improve accuracy in the cyber realm and could thereby reduce the risk of cyber fratricide.
Poor information flows can lead to the degradation or complete failure of an operation possibly at the cost of life or infrastructure. Network compromise or mission failure can also reverberate beyond the operation, affecting the entire organisation. Even when confidentiality is paramount, organisations can consider structural changes that improve sharing of information at critical points and using accurate, holistic mapping of cyber resources.
There is no defined warzone for cyberwar; conflict almost always involves friendlies and non-combatants. Secrecy and poor awareness in cyber operations can place outcomes, allies and citizens at greater risk of harm.