To take advantage of various unique services, users often create identities on multiple Social Computing Systems (SCS). To ease social sharing, many users connect multiple accounts to export content from one system to another (e.g. sharing recommendations from Yelp on Facebook). This generates ambiguities for the administration of privacy policies in that content might be posted to one service but accessed through another. This shared access is a challenge when protection policies may not perfectly match; how can the destination platform access and emulate the protection guaranteed by the originating platform, without breaching the privacy of the user?
Tarameshloo et al. examined this issue to develop a protection model for shared resources, by evaluating options for architecture and implementation of shared access policies. Secure Multiparty Computation (SMC) provides a method for access control policies that transcend the boundaries of any one SCS, and are enforced even after contents are migrated between systems. The practicalities are explored, including how a single shared policy can accommodate the different permissions applied on different services, using language that recognizes, honours, and integrates the terminology of different SCSs. SMC should achieve a fidelity of authorization and privacy policy, mechanism and states between services.
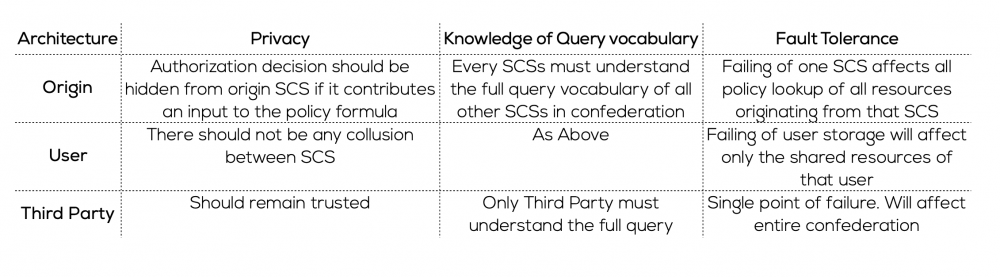
One of the challenges with SMC is the need to validate the privacy policy and access rights with exchange of information between the SCS, without disclosing either user information or details on the security policy of the SCS. The approaches to SMC of Private Function Evaluation (PFE) and Default Policies are evaluated in detail. Under PFE, using distributed evaluation each SCS permits other SCSs to query their authorization mechanism to determine the sites protection states. A PFE protocol computes that shared access function in a secure manner, keeping private the inputs of each SCS. The table below contrasts the approaches to PFE architecture where either a shared content originator, user, or a third party is responsible for managing polices.
The ‘Default Policies’ approach recognizes that most users will likely not independently specify a shared access policy for all content and so provides common and accepted standards. In this approach, SCS policies are not hidden, but rather publicly known. Each SCS determines whether the policies of other sites are trusted or not; in order to be deemed ‘safe’, the policy must ensure inputs are nondeducible – that is, they must remain private.
Secure Multiparty Computation can be used to protect the content that is shared across social computing sites. This method safeguards both user information and the protection states of the SCS. Both are desirable outcomes in a secure federated computing system.
Linking accounts online reduces security through dependency; mechanisms for determining the risk of a link can assist in managing the security of these arrangements.