There are resources on smartphones that are sensitive and need to be protected. For example, the camera or the ability to send a text messages are sensitive because they can be used maliciously. The Android operating system gives permission to applications to access sensitive resources on a case-by-case basis, based on a predefined security policy. In permission-based security, an app asks the system to use these resources. The permissions are enforced by code written by the programmers of Android. However, Android is a large piece of software written by hundreds of people over many years. As a result, there can be places where the permission checks are wrong or missing. This can lead to apps being inappropriately able to use resources or blocking valid apps from accessing resources.
The review of the security policy of a large program such as Android requires finding all the places in its code where permissions are granted. This is usually not possible to do manually. In order to tackle this, Shao et al. created and tested a technique for finding problems with policy enforcement in a large program. They developed an automated approach that produces a ranked list of problems for an expert to review.
Android controls access to resources like the camera by using “system services”. System services get requests from Android apps and do safety checks before allowing access to the resources. Android has a central service manager which controls access to all system services. The policy checking method uses this central manager to find all places where policies should be enforced. Then it finds all the possible ways the program can get to these services. Once the paths to these services are known, the security checks on these paths can be identified. To detect problems with the security policy, they compare the checks from different paths to the same sensitive resource. Any differences are flagged as potential problems for manual review.
They found 14 cases of inconsistent security policy enforcement in 6 different Android versions that could allow attacks. They discovered that there are more problems with newer versions. This is probably because of an increase in the number of “system services” as more features were added. They also found that disabling “hidden interface” access to resources for applications would reduce the number of flaws in Android. Many weaknesses in Android also exist because multiple “system services” control the use of one resource. They recommend having only one service to protect each resource.
Any organization that has large programs could use this approach to find problems with security policies. Programmers can make mistakes, so double checking policy enforcement is recommended to make sure a system is secure. Limiting access to sensitive resources and disabling the use of hidden interfaces can also reduce the number of problems.
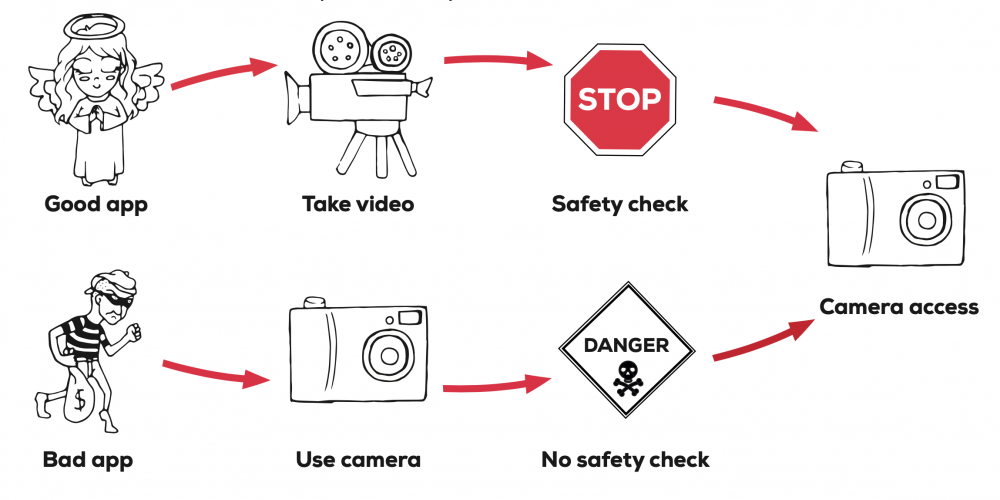
Automated techniques can help find problems with policy enforcement in large permission-based programs like Android.