System attacks at the physical level can bypass security software and operating system controls. This makes them particularly dangerous as they can make any system vulnerable. It has been widely assumed that such an attack required executing a malicious program directly on the target computer. This is not necessarily the case.
Computer memory makes use of tiny capacitors that temporarily store an electrical charge. An uncharged capacitor stores a ‘0’ and a charged capacitor stores a ‘1’. These bits of data are bundled together into large arrays to store complex information and instructions for the computer. Modern memory packs data storing capacitors very closely together and uses smaller electrical charges because of the demands of greater speed and miniaturization. The proximity means that it is possible for small amounts of electricity to overflow into neighbouring capacitors. Using smaller charges means that this might be enough to change the value of a capacitor from a ‘0’ to a ‘1’. Rowhammer attacks take advantage of this by aggressively charging and discharging capacitors in the hope their neighbours will change value. Changing a ‘0’ to a ‘1’ in some memory locations could reverse access restrictions, negate encryption etc.
Tatar, Krishnan Konoth, Athanasopulos, Giuffrida, Bos and Razavi demonstrated that it is possible to deliver a Rowhammer attack via a network connection. Ethernet network cards equipped with remote direct memory access (RDMA) allow devices on a network to exchange data directly in the devices’ main memory. This mechanism is used in high-performance networking operations such as data centers or for cloud services. The researchers showed that with a bandwidth speed of 10 Gbps, attackers can deliver 560,000 packets per 64 milliseconds to the memory on a remote computer. At this speed a Rowhammer type attack is possible and by changing data stored in restricted memory locations they could gain the ability to execute commands on a system. Tatar et al. demonstrated the exploitation of this flaw against a RDMA-enabled short-term application memory system on two test machines. They were able to store sensitive data in vulnerable memory locations; corrupting data and compromising the systems.
Tatar et al. proposed a solution that isolates the specific memory bits vulnerable to these attacks. This tool uses a novel memory allocation strategy to insert guard zones around vulnerable bits on a memory card and has a low impact on a system’s performance.
Current mitigations based around preventing direct code execution are not necessarily effective against Rowhammer type attacks. This new method of this attack removes the need for direct access on the targeted machine.
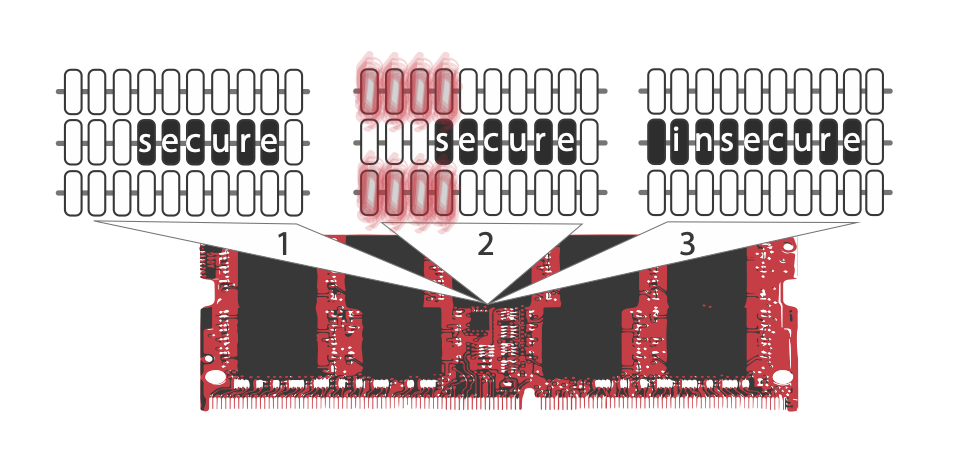
Physical attacks like Rowhammer which overcome security controls can now be performed over the network.