The growing use of the Android platform has been accompanied with an increase of mobile malware. Malware threats range from simple user tracking and disclosure of personal information to advanced fraud and premium-rate SMS services subscription, or even using the resources of the device for the benefit of an attacker as part of a network (or `botnet`) of infected smartphones. Anti-virus software forms part of the effort to overcome malware on mobile devices. However, the effectiveness of anti-virus programs is in question. Statistical investigation provides a first step to show the state of the art in anti-virus solutions for the mobile application ecosystem to identify the current gaps and issues.
Allix et al. analyzed a set of both benign applications (apps) and malware in the Android ecosystem that were developed over recent years and downloaded in 2014. They collected over 500,000 free Android applications from user markets including the official Google Play and some other unofficial app stores including AppChina, Anzhi, Slideme, FreewareLovers, ProAndroid, F-Droid, and 1mobile. In addition, they collected some apps through Bittorrent and malware from the Genome academic dataset.
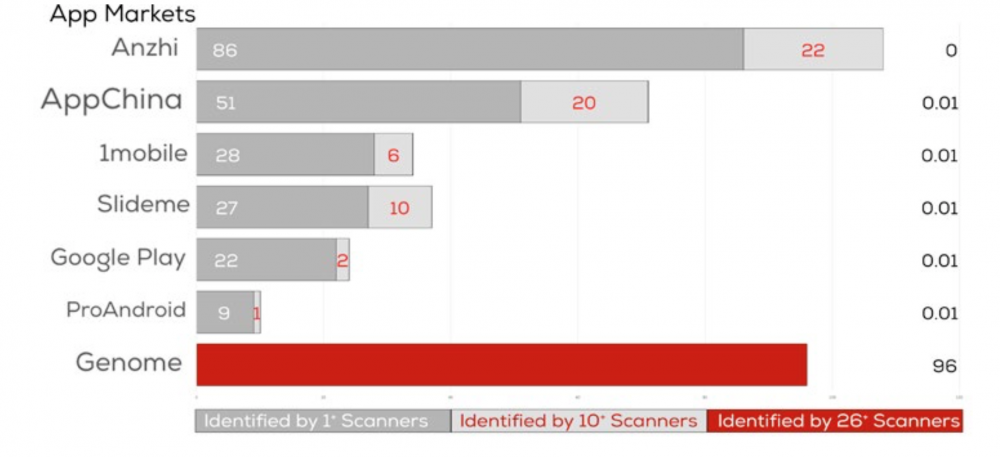
These apps were scanned with the approximately 40 antivirus products hosted by VirusTotal, including those from market leaders such as McAfee and Symantec.
The results show that no single antivirus product can identify all existing malware. Only a small subset of widely known malware are recognized by a large number of antivirus software. As shown in the figure below, there is great variation in both the percentage of apps detected as malware and also the agreement between antivirus products on what is malware. From the Genome dataset of known malware, 96 percent of samples were detected as such by more than 25 anti-virus products. However, the scanning results show that only small subset of malware downloaded from active app markets was recognized by a majority of anti-virus software.
The study also examined information on app production, for clues into malware detection. The analysis of packaging dates of applications provides some insight into malware development. It shows that malware development is often a standardized process that aims to produce a large number of malware at once. Moreover, malware writers like other developers, follow a consistent work schedule, suggesting an industrial rather than hobbyist approach to building malware.
The research also studied the developer’s digital certificate of each app, assigned before a product is uploaded to an app store. There is no distinct pattern between malware and benign applications, suggesting that studying only the application certificates will not contribute to the detection of malware. There is a clear need for more consistent and stronger anti-virus products, to improve on the low level of agreement in malware detection by existing anti-virus products in a real world environment. If malware is developed in mass produced batches from an industrial process, as this study suggests, the detection industry has to improve the general standard of detection.
Malware production is happening on an industrial scale and our current detection tools are inconsistent and a poor defensive solution to the problem.